Articles in Data Storage Types
♪ BDE Compatibility of data organized under certain regulations, providing general principles for the description, storage and manipulation of data independent of applications. [GOST 20886 85] OBD database, which is sufficient Repertoire of Technical Translator - (database) Streamlined computer information. There is a special computer programme called a database management system (database manaqement system, DBMS) that is used to streamline the database Business Terminus - DATA database, a data set created or obtained by a computer. DATAs are usually stored on MAGNIUM DISCASSE…
Bookkeeping and accounting services for nonprofit organizations near me.

The main objective of the computer system is to implement programmes. Programmes, together with data they have access, should, at least partially, be kept in operational memory. The operational system has to meet the challenge of sharing memory between the user processes and the components of the LO. This is called memory management. Thus, memory (storage, memory) is an essential resource that requires careful management. In the recent past, memory was the most expensive resource. Part of the DS, which is responsible for memory management, is called memory manager. The physical…

The Group launches the Heotbox Repository based on the Business Game. The product is designed for those who have a need not only for storage but also for the distribution of a large number of files, primarily for the owners of visiting media services, online MI and UGC-content sites and mobile application developers, CNews has been informed by the Group. Service starts in beta mode, companies are invited to participate in closed testing. TheWarehouseis intended for downloaded services that require the storage and distribution of digital content, and will free the business from…
Markets and Markets predict the growth of the cloud storage market to $74, 94 billion by 2021. Markets and Markets studies show that cloud data storage markets will grow from $23,76 billion in 2016 to $74, 94 billion by 2021, an average growth of 25.8 per cent per year. The growing demand for hybrid cloud solutions, the need for business mobility, the need for easy introduction of cloud technologies fuel the growth of cloud markets. Markets and Markets estimated that North America had the largest share of the cloud market in 2016, while the Asia-Pacific region (APAC) will show…

An IFI printer with a TL-PS310U data storage function is ideal for sharing access to USB home or work network facilities. The device is compatible with most printers and multifunctional printers on the market and enables these devices to be used and operated jointly with the computer network. The device can also be connected to and operated with 4 USB-based devices, such as scanners, flash-point maps, columns or web cams, using USB a dock connected to the server. These devices will be accessible from any point of the network and even through the wireless connection if the printer…

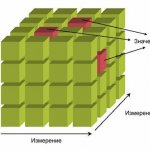
Lecture onFISICUS ARRANGEMENTS, DATA Producer: St. Lecturer of the Church L.S. Lecture Plan 1. Physical access to the database & 1. FISICAL ACCESS TO THE DATA BASE 1.1. The volumes of modern databases and their location are presented in the figure. 1. The user interacts with the database system by launching instructions. The strategic selector will transform the user team into the most effective form for implementation. The converted requirement shall activate the buffer control device controlling the movement of data between operational memory and disk. The file controller…

The issue of long-term storage of digital photographs is somewhat deeper than it may appear at first sight. Unlike “operative” files, digital photographic archives should be guaranteed to remain intact for years and decades. Would it seem easier? Many different launchers are available: optical CDs, DVD and BlueRay (BR) disks, all possible flashes and memory maps, routine hard drives and even remote file repositories, so-called file exchangers. The main problem of long-term storage of digital images is the reliability of the carriers, and the capacity, speed or convenience of…
Data should be stored separately from software. Data storage with programmes has a risk of accidental damage to programmes, which can also lead to the destruction of the operating system. If possible, usersfiles should be better stored on CD C, where the operating system files are located. Well, if there s only one hard drive C on the computer, you can recommend a folder, for example, with the nameD:. Then we need to make a label to this folder (the right button of the mouse -Create the label) and rename it, for example, toDisk_D. The label should be placed on the desk of your…

2002 No. 4 When designing modern microprocessary systems, developers often face problems in choosing the appropriate type of replacement device. Frequently there are contradictory requirements for the replacement device. As a result, in many cases the memorial area is divided into a number of separate blocks: Permanent memory. Relatively slow memory, intended primarily to store the work programme when eating off. In high-produced systems, a copy of the contents of the ELV in the fast-acting PES is being carried out in the process of operation. Rapid OPC. Designated for rapid…
Can I keep my fortune in Redux? Should I always use a setState from React? There is no “right” answer to this question. Some users prefer to store all the data in Redux in order to maintain a fully serial and controlled version of their application over time. Others prefer to make non-critical (UI) data, such as “is this dropdown currently open” to the component. Better use the component. It s your job, as a developer, to decide which parts of the state are your app and where each of them is stored. Find the balance that suits you and implement it. Some non-public rules are…

Name HDD jbod Raid z Raid 10 price with VAT LINA DND 1 Tb 192 1056Tb 816Tb 528Tb 15 500, roubles. Safeguards and launchers of the Safeguards are 2 years old. Dévlain provides a complete service cycle from the installation of the server desk to the connection and construction of the equipment. The cost of support includes the travel of company specialists to launch PCBs. 12 to 24 monthstechnical service and 2 emergency exits, if necessary. Also for the duration of the guarantee period, the company carries out remote monitoring of the CCD (with technical capacity). Please note…
Readitorial data storage and security is one of the most important problems of any computer owner. And when there s too much data, another problem is the problem of information management. Our reader, Vitaly Goubsky, tells us how to store files so that any carrier in any operating system and without any additional software can always be seen in the right order. The authors script and puncture are retained. Data storage and security is an important problem for any computer owner. And when data are too much, another problem is the problem of information management. Some of them…
DataSync HTTP API is designed to synchronize these applications on different devices and platforms. API can synchronize, for example, user designs, open deposits, current status of games and other data. Synchronization of data is carried out through the intermediate storage facility (hereinafter the synchronization storage facility). The synchronization store is located on the Yandex servers. It is used to store the current status of the annex as well as the history of all changes. The task of the developer is to synchronize the local data of the annex (data, for example, in…

By agreeing to the processing of personal data in accordance with Federal Personal Data Act No. 152-FZ of the year, you confirm your consent to the processing of personal data by the 3-D News Unit: collection, systematization, stockpiling, storage, clarification (update, change), use, blocking, decoration, destruction. We, OO 3D News (OG 382, yur. address: 1,21151, Moscow, Kutuzwa, p. 22, p. 1), guarantee the confidentiality of the information we receive. The processing of personal data is carried out only to identify participants in the competition conducted on the websites…

Data exchange from 1C 8 is divided into 2 parts: manual and automatic import of goods from 1C; automatic export of orders from the site; Russian imports from 1C8 (CommerceML 2.03 and above) are essentially similar to imports from the previous version. In the 1C itself, the itemService,Web data exchange, should be selected. Create the development through theWeb-based data exchange building. It should be pointed out in the construction that this would beunloading of goods(providing the required box) as well as the type of data interchange:Getting into the catalogue

Hello! Finally, I found time to please you with new material! I m sorry I haven t written that long. The thing is, I ve been working on one project I ll tell you about in the future. Why do you have to buy a new hard drive? Everyone may have their reasons, but this basically means that the speed of work and downloading of programmes has decreased markedly, or there is a lack of room for new information on the computer. No matter what reason it takes to buy a new hard drive, everyone has something to think before they buy

TheStorage of Danesis a group of Safedata companies, which is the operator of the date-centre network. Since 2017, 100 per cent of the shares have been owned by Rostelcom. In 2007-2010, the group built and commissioned the Moscow-I date centre, with the declared level of TIER 3, located at Moscow, the Ostipov pd, d.22. The date-centre meets the requirements of TIA-942 level 3 and is classified as data centres with secure network infrastructure. The Centre is intended to serve clients with high requirements for the reliability of equipment, the capacity of communication channels…

AggreGate Server stores a large number of data collected and internally generated on the network of devices, namely: The definitions and configuration of the server and system resources modules of the Registry of All Systems Operations and Events of the Historical Metrics of the Permanent Events from the Synthetic Internal Metrics and Events Network All data stored by the server are divided into two main groups: configuration and events. This simple separation provides absolute flexibility in adding new types of devices and business objects without altering the data storage…

Cluster Node: domestic production server Etegro (2 AMD Opteron 6320, 16 GB RAM, 4 HDD) The data storage systems currently used in practice in Russia are conditionally divided into three categories: Very expensive high-end CCB; Middle ranges (triing, HDD, hybrid decisions); And economic clusters based on SSD Massives and HDD Massives fromhouseholddisks often collected by their hands. And it s not that the last decisions are slower or less reliable than the Hayland. It s just another approach that doesn t always fit for the same bank, for example. But it s good for almost all…

Question of the answer, in accordance with the requirements of the law, to correct a technical error: a contract for the purchase and sale of forest land in a lease? The erroneous document should be translated into deleted status, explaining why this action is being implemented. Further reintroduce the document to the relevant section of the EGIS for wood accounting and transactions. How and at what time do you want to report the termination of contracts (hards, sale)? The treaty may be terminated by agreement of the parties or by court decision

Solid reservoirs have a number of advantages over traditional hard drives: energy consumption, time and speed of access. And a year from now, the main flaw becomes less visible - SSD is cheap. Elvin Coxs report to the Committee of Electronic Engineers (JEDEC) addresses long-term storage of hard-core data and highlights the difference between household products and industrial samples. Normal solid reservoir for ordinary consumer at 40° C and storage temperature at 25° C will keep information for 105 weeks, it s about two years

First parameter is system ID. This is the number defining the general memory segment of the system. The second is the access regime, which is very similar to the fopen mode of access. Access to the segment can be obtained by four means: thearegime allows only for reading; thewregime allows access to the reading and recording segment; theccreates a new segment and, if it already exists, attempts are made to open it for reading and recording; thenregime creates a new segment and, if it already exists, reports a mistake. Third parameter is the permit for the segment. There s a…

MOSKWA, July 24th. / TAS/. The new European Union regulation on the storage of personal data could not affect Russian companies because of the absence of a document binding on the laws of another State. This view was expressed by the TAS by Herman Climenko, President of the Russian Federation, on Internet development issues. Previously, the Office of Internal Affairs reported that the EU would introduce new data processing standards in May 2018, with company customers being stored only to ensure national security and the rule of law and with appropriate evidence from the intelligence…

Until recently, all DSBs with structured data (and not only them) could be divided into two categories: the stored records in the design format and the stored records in the column format. This is a fundamental difference that affects how the tables look at the level of internal storage of the DSB. For a long time, CBD Teradata was in the first group, but with the release of the 14th version, it was possible to determine how to store the particular table in columns or lines. Thus, hybrid storage has emerged. In this article, we want to describe why this is necessary, how it…

From a technical point of view, the receipt of a bank card to pay is always the write-off process from the buyers map. This write-off process is calledpayhere. Payment may consist of one operation or sequence of operations. Depending on the terms and requirements of the sellers business, payments may have different characteristics. To ensure the successful payment process, the seller needs to understand in advance how and under what conditions the write-offs from the buyers map will take place

Products and technologies Dell for data storage. Establish your own data-processing and storage infrastructure through our integrated data collection, consisting of the product line Dell Compellent, EqualLogic and PowerVault. Regardless of whether you need a data storage network (SAN), a web-based data storage system (NAS) that is directly connected to the data storage system (DAS) or other data storage systems, Dell Corporation provides exceptional simplicity, attractive value, high productivity and accessibility to its decisions

The attitude of hard drive manufacturers towards hard-core reservoirs is not a secret: both Seagate and Western Digital have always argued that such devices can serve only certain market niches but cannot compete with hard drives. Executive Director Seagate went further: he said no one uses SSD as data storage devices. Solid reservoirs are now used in various customer personal computers. Many laptops use SSD as major data reservoirs, productive desktop PCs use solid storage devices as PP loaders and frequently used programmes. While it is quite clear that many types of computers…

As a rule, if you are developing data storage systems, such as a file system or database, one of the main problems is how to store data on a disk. In design, you must take care of a number of tasks. For example, the allocation of space for objects you re going to keep. Also on data indexing, so that you don t have to worry about what s going on when you want to expand the existing facility (e.g. adding data to the file) and about the fragmentation that occurs when old objects are removed and new ones take their place. All of this leads to a lot of difficulties, and solving frequent…

The basic layout of computer parts and the connection between them are called architecture. The computer architecture describes the composition of its component, the principles of its interaction, and their functions and characteristics. Virtually all universal computers reflect the classic neuman architecture presented in the scheme. This scheme is very common for both microwaves and miniwaways and general-purpose computers. Rhys. 1 Personal computer architecture, see the devices more detailed. The main part of the system fee, a microprocessor (MP) or CPU (Central Processing…

The personal data of the employees include not only information generated during the work process, but also any other information concerning the personal life of both the staff member and his family. As for the personal data of the worker, the law clearly defines the concept of personal data. Regulation and control in this area is important to both the employer and the firms employee. Personal data in accordance with article 3 of Federal Act No. 152 on personal data are information that is relevant to a citizens particular or determined on the basis of such information, including…

The only storage unit in the file may be: an article, a card, a sheet of paper, affixed or removed, a cover, a note, a magazine, a record of the EMS. Depending on the type of card, the shape of the card is changed. It could be a card box, paper files and articles, notes, computer databases. One of the main requirements for the card is the easy reading of the text. This natural requirement is not always met if the printing machine is not used. When CARTOC CARTOC POLICY is completed, it s very important to use the FUEL MASHINE

And the computer text looks like: The man sees the text: The computer again sees the set “0” and “1”: 0100 1001 0101 0100 0010 1101 0 0101 0 0010 0110 0110 1001 0010 0 0 0 0101 0101 today, we will not be able to understand the subsets of the calculations and changes, see the process in general. Where information is stored when the information is stored in the computer (recorded), it is stored on a special device, the data repository. Usually the data reservoir is a (vinchester). The hard drive is called the device because of the design. There is one or more solid pancakes (metal…

Decided to write a small article on data storage networks (CDDs), the topic was quite interesting, but it was not solved in Habré. I ll try to share personal experiences in building and supporting SAN. What is it? The data storage network , or Storage Area Network, is a system consisting of data storage devices - disk, or RAID - masses, ribbons, etc., the data transmission environment and the servers connected to it. Usually, large companies with advanced IT infrastructure are used to secure data storage and fast access. Simplifiedly, the CCB is a system that allows the servers…

Virtualization provides users with many advantages, most of which: better use of accessible disk space; simplified management, high productivity; and powerful data remediation tools. Server level at server level, virtualization can be achieved through software that is permanently located on the server and independent of the reservoirs. With this software, the operating system forces the server to act as if it was linked to a specific type of storage device, although the server actually maintains a connection to the virtual disk. Virtualization at the server level can be used…

Despite the increasing attacks on viruses, as well as the cunning of hackers, the Internet is a reliable and affordable way to guarantee the integrity of information. But it s worth remembering that you can only be sure of the security of the data if you choose the right approach. If you keep important information on your work or home computer, there s a great risk that someone else can access it. There is also a possibility that data may be lost due to accidental disposal or physical destruction of the computer. The storage of information online completely excludes such scenarios…

Each modern Operation System (OS) has a component called the File System. This component is part of the PPE nucleus, and it covers items such as Files and Fish directories. There are many different Fails, different methods and algorithms used, but some basic functions are available in most Fail Systems: the Failing System leads in some form the Faylov Displacement Table (FAT) - information linking logic files to the storage unit numbers. For example, FAT can claim that File1 is stored in 5 disk blocks with 123400, 123405, 123401, 1, 123456, while File2 is stored in 6 disk…

What s the big data? The answer to this question depends on who and when asked. We ll get a common user: fifteen years ago, an average home computer was computed by several gigabytes, now hundreds and even thousands of hygabytes. More serious example: Boeing Jet sensors generate about 10 TB data from each engine for only 30 minutes. I mean, a plane coming from Moscow, say, to Novosibirsk in four hours will give us about 160 TB data. And it s only from one flight. For dessert, it is possible to calculate how many of the data left to humanity the past Olympics in Sochi: hundreds…

The amendments to the Personal Data Act require, as of 1 September 2015, the retention and processing of the personal data of Russians in Russia, D. Abramov/Vedomity, if the company stores the personal data of the Russian base, may use a copy of the database abroad, are explained by the Ministry of Communication to the amendments to the Personal Data Law (Vedomnesty). If the organization complies with the requirements of the cross-border transmission of data that it has collected in Russia into the so-called primary database, it may transfer them abroad to a secondary database…

When you measured the amount of data that you re planning to reserve, the next logical step is the choice of an effective data host. Ideally, the volume of the host corresponds to the volume of data. For example, a small amount of important data you can replicate anywhere, and the music collection requires a large volume of a host, external HDD, or a CD set, DVD, depending on your desire, convenience. A whole hard drive, of course, needs to be copied on another hard drive or server. Analysing the convenience and rebuilding, of course, when you choose the host, you need to take…

Who s gonna keep data on the purchase or payment of services in the form of an electronic check? The cheques are stored both in the tax authorities and in the cash register. The buyer will be able to find his cheque by the appropriate service on the official website of the Russian Federation or by using a free mobile application. It is important that the new technology provides a citizen with additional protection of his/her rights as a consumer, not only through the possibility of obtaining an electronic cheque, but also by itself promptly and conveniently checking the legality…

One of the most sophisticated archives, with a huge volume of complementary tools for joint work, a web-based editor of office and other types of documents and a high synchronization rate. It s perfect as a photo archives. Very often, the service is used with a multi-user job on one office file. A special authentication regime is provided for organizations using the Single Point System (SSO). The relatively small amount of free space, 15 GB, is a source of disappointment, and it is also consumed by letters stored in Gmail. Of course, if desired, the cloud disk could be increased…

Valuable books, works of art, copies of films and all possible documents will find a secure and durable peace in the underground bunker near the North Pole. According to the Norwegian Broadcasting Corporation, the archives of different countries (now Brazil and Mexico are already involved in the project in addition to Norway) will be located in an abandoned coal mine near the town of Svalbard, the centre of business, tourism and scientific life of the Spitzbergen. The most interesting thing about this project is that the digital data will be stored on analogs. I mean, on the…